- ClickFix makes use of faux CAPTCHA screens to trick customers into launching malware through easy keyboard instructions
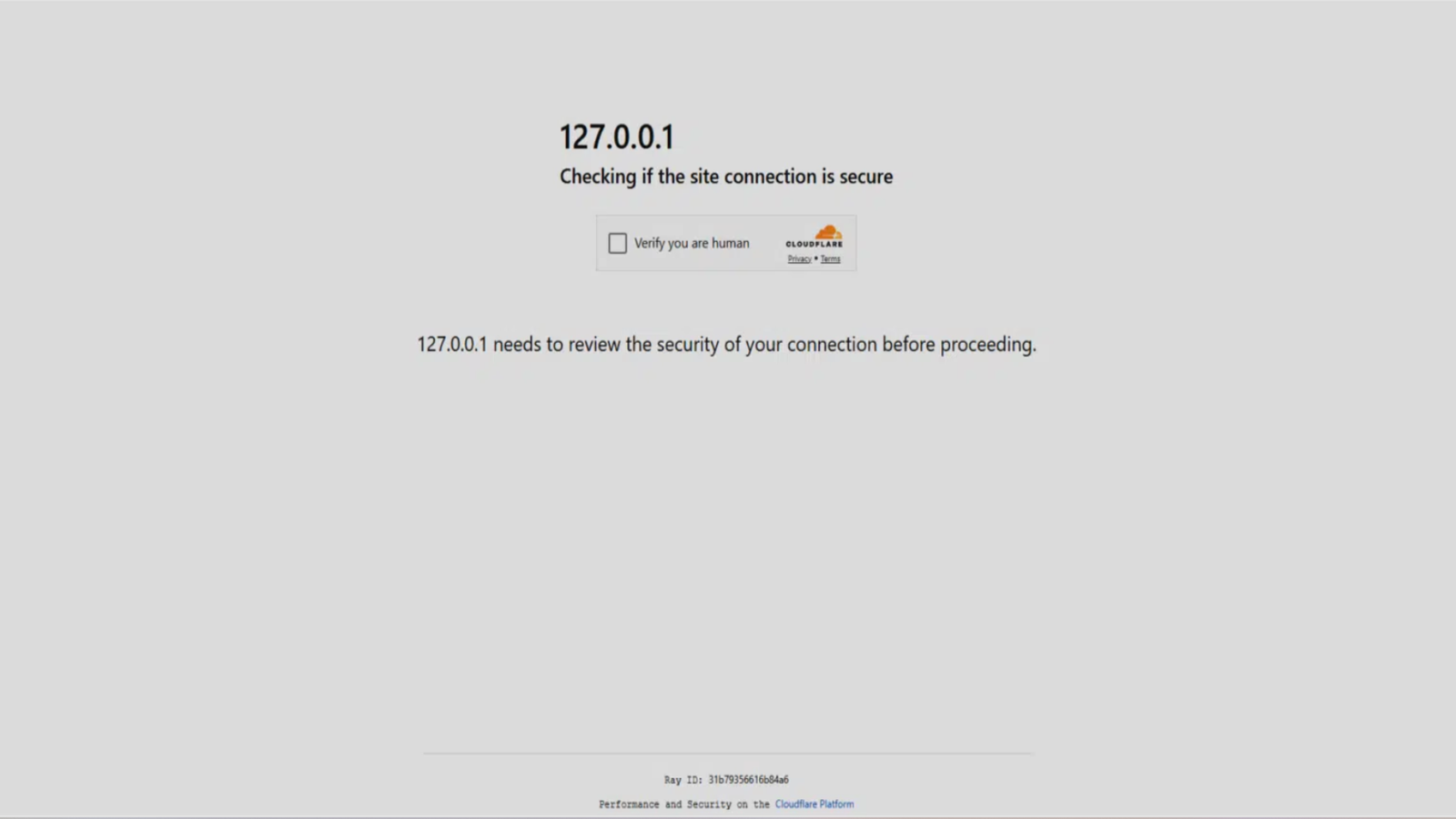
- The phishing web page mimics Cloudflare completely, proper right down to Ray IDs and safety padlocks
- Clicking “Confirm you might be human” begins a course of that silently infects your machine with malware
A complicated but deceptively easy phishing method is at present circulating, utilizing faux Cloudflare CAPTCHA pages to contaminate customers with malware.
New analysis from SlashNext claims the method, referred to as ClickFix, preys on acquainted web conduct, tricking customers into executing instructions that set up malicious software program.
ClickFix works by presenting a counterfeit model of Cloudflare’s Turnstile CAPTCHA web page. Every thing from the visible structure to technical parts just like the Ray ID identifier is convincingly replicated.
Hinges on a immediate that customers will ordinarily not scrutinize
The phishing web site could also be hosted on a site that intently resembles a reliable one, or on an actual web site that has been compromised.
When customers land on the web page, they’re prompted to tick a field labelled “Confirm you might be human.” This step seems routine and raises no suspicion – however what follows is the core of the rip-off: customers are guided by a set of directions – urgent Win+R, then Ctrl+V, and at last Enter.
These steps appear innocent, however they execute a PowerShell command that has already been silently copied into the consumer’s clipboard.
As soon as executed, the command can retrieve malware akin to Stealc, Lumma, and even distant entry trojans like NetSupport Supervisor.
Signal as much as the TechRadar Professional publication to get all the highest information, opinion, options and steerage what you are promoting must succeed!
"ClickFix is a social engineering assault that methods customers into operating malicious instructions on their very own units – all beneath the guise of a routine safety test,” mentioned safety researcher Daniel Kelley.
What makes ClickFix particularly insidious is the way it turns commonplace safety expectations into weapons. The padlock icon, acquainted CAPTCHA format, and a legitimate-looking URL all serve to lull customers into compliance.
This exploits what researchers consult with as “verification fatigue”, a consumer’s tendency to click on by safety prompts with out correct scrutiny.
The trick doesn’t depend on exploiting software program vulnerabilities, however fairly on abusing belief and routine conduct.
The phishing web page is delivered as a single HTML file, however incorporates embedded scripts and obfuscated code designed to carry out clipboard injections.
As a result of it leverages reliable Home windows utilities and doesn’t obtain executables, it could evade many conventional detection instruments.
Commonplace defenses, like antivirus software program or endpoint safety, are sometimes geared towards catching suspicious downloads or binaries. However on this case, customers are tricked into launching the menace themselves.
This highlights the necessity for superior malware safety with zero-hour protection, able to detecting clipboard injections and pretend CAPTCHA screens in actual time.
You may also like
- Downloaded one thing dodgy? These are one of the best malware removing instruments
- Nail the fundamentals with one of the best firewalls accessible now
- OpenAI says it disrupted not less than 10 malicious AI campaigns already this 12 months